Integrated Security Suite
We combine cutting-edge technology with strategic planning to safeguard your
critical assets and ensure your peace of mind.














TwinTech Solutions transcends the realm of traditional security consulting. We serve as a trusted advisor and a steadfast partner, leveraging our comprehensive experience and proven methodologies to guide your organization through a transformative cybersecurity journey.
We harness our market-leading technical expertise to offer a full suite of cyber consulting and advisory
services, designed to help your vision become a thriving reality. Learn more about us.
![]()
Senior VP of Strategic Support from the B2B Lending Solution provider company.
![]()
![]()
IT Head & Director from the Digital Transformation Company.
![]()
![]()
IT Security Head from Manufacturing Industry.
![]()
![]()
CEO from the Mortgage & Financial Services Industry.
![]()
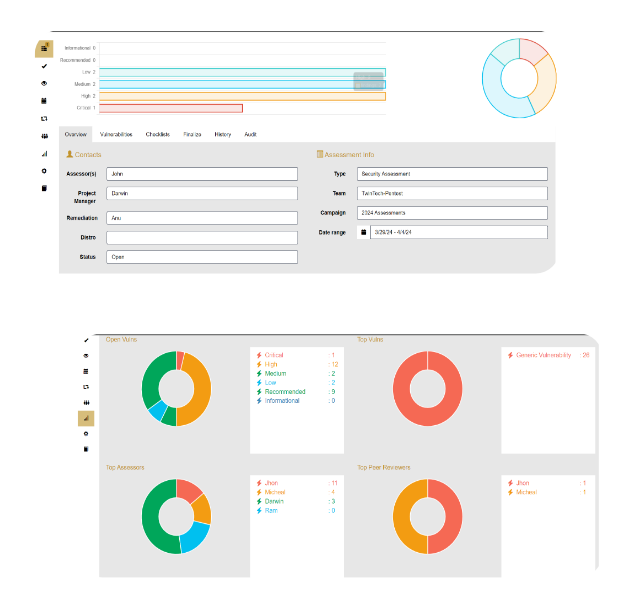
Upgrade from outdated PDF penetration test reports to a human-driven penetration testing method for unmatched intelligence and continuous security testing.
Driving technology for leading brands












